2.3. Substitution Ciphers#
A substitution cipher is a cipher in which blocks (e.g. a single letter, or a pair of letters, or word) of the plaintext are replaced by another unit of text.
2.3.1. Example 1#
Substitute letters with emojis
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
🐜 |
🐝 |
🐪 |
🐉 |
🐘 |
🦩 |
🦒 |
🦛 |
🐄 |
🐙 |
🦘 |
🦙 |
🐒 |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
🐢 |
🦉 |
🦚 |
🦆 |
🐇 |
🐨 |
🐅 |
🦋 |
🐳 |
🦃 |
🦌 |
🐖 |
🦓 |
Plaintext:
SECRET MESSAGE
Ciphertext:
🐨🐘🐪🐇🐘🐅 🐒🐘🐨🐨🐜🦒🐘
2.3.2. Example 2#
Substitute words with emojis
Plaintext |
A |
ALL |
GLITTERS |
GOLD |
IS |
KNOWLEDGE |
MEN |
NOT |
|---|---|---|---|---|---|---|---|---|
Ciphertext |
🎵 |
🔮 |
✨ |
🏅 |
🪩 |
🔭 |
👨 |
❗ |
Plaintext |
ROSE |
SWEET |
THAT |
UNDER |
VERY |
WORLD |
YOU |
|---|---|---|---|---|---|---|---|
Ciphertext |
🌹 |
🍬 |
🎩 |
⛳ |
🍒 |
🌏 |
🫵 |
Plaintext:
ALL THAT GLITTERS IS NOT GOLD
Ciphertext:
🔮🎩✨🪩❗🏅
2.3.3. Example 3: Caesar Cipher#
Substitute letters with letters
A Caesar cipher is a simple substitution cipher that encrypts text by replacing each letter with a letter that is a fixed position later in the alphabet. An encryption is defined by a shift.
For example, a shift of 2 means that every letter will be shifted across 2.
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
Plaintext:
I THINK THEREFORE I AM
Ciphertext:
K VJKPM VJGTGHQTG K CO
2.3.4. Example 4: Simple Substitution With Key#
Substitute letters with letters
When substituting letters with letters all we need is a normal alphabet that maps to a mixed alphabet. We can create a mixed alphabet by using a key. In this simple scenario we take all the letters in the key and move them to the front of the alphabet. For example, let’s use the key \(\textcolor{red}{IMAGINATION}\). You’ll notice that some letters repeat. If we take out repeating letters we get \(\textcolor{red}{IMAGNTO}\). Now what we’ll do is we’ll take these letters and move them to the front of our alphabet.
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
\(\textcolor{red}{I}\) |
\(\textcolor{red}{M}\) |
\(\textcolor{red}{A}\) |
\(\textcolor{red}{G}\) |
\(\textcolor{red}{N}\) |
\(\textcolor{red}{T}\) |
\(\textcolor{red}{O}\) |
B |
C |
D |
E |
F |
H |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
J |
K |
L |
P |
Q |
R |
S |
U |
V |
W |
X |
Y |
Z |
Plaintext:
UNITED WE STAND DIVIDED WE FALL
Ciphertext:
UJCSNG WN RSIJG GCVCGNG WN TIFF
If you know the key you can ‘unlock’ the encryption because you can determine what the mixed alphabet looks like.
Code Challenge: Encrypt: Simple Substitution Cipher With Key
Write a program that asks the user for a key and a plaintext message. Your program should then display the corresponding ciphertext message. You can assume all inputs will be given in upper case.
Example 1: Key is IMAGINATION
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
\(\textcolor{red}{I}\) |
\(\textcolor{red}{M}\) |
\(\textcolor{red}{A}\) |
\(\textcolor{red}{G}\) |
\(\textcolor{red}{N}\) |
\(\textcolor{red}{T}\) |
\(\textcolor{red}{O}\) |
B |
C |
D |
E |
F |
H |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
J |
K |
L |
P |
Q |
R |
S |
U |
V |
W |
X |
Y |
Z |
Key: IMAGINATION
Plaintext: UNITED WE STAND DIVIDED WE FALL
Ciphertext: UJCSNG WN RSIJG GCVCGNG WN TIFF
Example 2: Key is ACKNOWLEDGEMENT
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
\(\textcolor{red}{A}\) |
\(\textcolor{red}{C}\) |
\(\textcolor{red}{K}\) |
\(\textcolor{red}{N}\) |
\(\textcolor{red}{O}\) |
\(\textcolor{red}{W}\) |
\(\textcolor{red}{L}\) |
\(\textcolor{red}{E}\) |
\(\textcolor{red}{D}\) |
\(\textcolor{red}{G}\) |
\(\textcolor{red}{M}\) |
\(\textcolor{red}{T}\) |
B |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
F |
H |
I |
J |
P |
Q |
R |
S |
U |
V |
X |
Y |
Z |
Key: ACKNOWLEDGEMENT
Plaintext: NOT ALL THOSE WANDER ARE LOST
Ciphertext: FHR ATT REHQO VAFNOP APO THQR
Solution
Solution is locked
Code Challenge: Decrypt: Simple Substitution Cipher With Key
Write a program that asks the user for a key and a ciphertext message. Your program should then display the corresponding plaintext message. You can assume all inputs will be given in upper case.
Example 1: Key is IMAGINATION
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
\(\textcolor{red}{I}\) |
\(\textcolor{red}{M}\) |
\(\textcolor{red}{A}\) |
\(\textcolor{red}{G}\) |
\(\textcolor{red}{N}\) |
\(\textcolor{red}{T}\) |
\(\textcolor{red}{O}\) |
B |
C |
D |
E |
F |
H |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
J |
K |
L |
P |
Q |
R |
S |
U |
V |
W |
X |
Y |
Z |
Key: IMAGINATION
Ciphertext: UJCSNG WN RSIJG GCVCGNG WN TIFF
Plaintext: UNITED WE STAND DIVIDED WE FALL
Example 2: Key is ACKNOWLEDGEMENT
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
\(\textcolor{red}{A}\) |
\(\textcolor{red}{C}\) |
\(\textcolor{red}{K}\) |
\(\textcolor{red}{N}\) |
\(\textcolor{red}{O}\) |
\(\textcolor{red}{W}\) |
\(\textcolor{red}{L}\) |
\(\textcolor{red}{E}\) |
\(\textcolor{red}{D}\) |
\(\textcolor{red}{G}\) |
\(\textcolor{red}{M}\) |
\(\textcolor{red}{T}\) |
B |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
F |
H |
I |
J |
P |
Q |
R |
S |
U |
V |
X |
Y |
Z |
Key: ACKNOWLEDGEMENT
Ciphertext: FHR ATT REHQO VAFNOP APO THQR
Plaintext: NOT ALL THOSE WANDER ARE LOST
Solution
Solution is locked
Code Challenge: Extension: Caesar Cipher
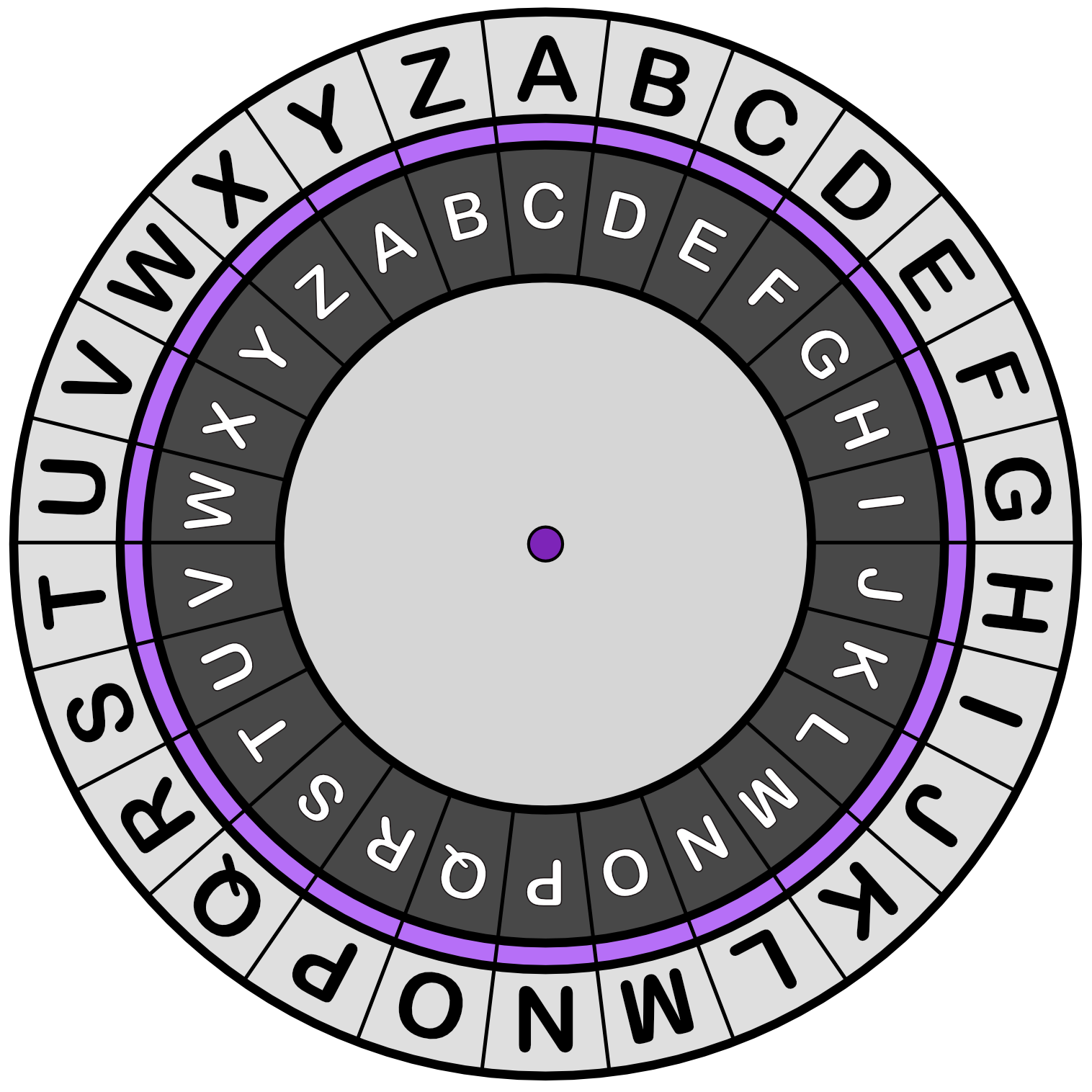
A Caesar cipher is a simple substitution cipher that encrypts text by replacing each letter with a letter that is a fixed position later in the alphabet. An encryption is defined by a shift.
For example, a shift of 2 means that every letter will be shifted across 2.
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
Plaintext |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Ciphertext |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
So CAT would become ECV.
Write a module called caesar that can be used to encrypt and decrypt using a Caesar shift. You will only be given capitalised letters. Any character that is not a capital letter should not be encrypted.
You should be able to import your functions from your module into your main script main.py. Your module should contain the following 2 functions.
Encrypt specification (written in caesar.py)
name:
encryptparameters:
plaintext(str),shift(int)return: the encrypted text (
str)
Decrypt specification (written in caesar.py)
name:
decryptparameters:
ciphertext(str),shift(int)return: the decrypted text (
str)
You will notice that in a Caesar cipher the alphabet wraps i.e. the next letter after Z is A. For this, the modulus (%) operator can be quite useful. The modulus gives you the remainder, and can be used to wrap numbers. For example 27%26 is 1, because the remainder when you try and divide 27 by 26 is 1. This will allow you to map the 27th letter in the alphabet back to the 1st letter in the alphabet.
In your main.py file you should write a program that asks the user to enter some text, then specify whether they want to encrypt or decrypt the text and then specify a shift. Your program should then reveal the encrypted/decrypted message.
Example 1 (running from main.py)
Enter text: CAT
Enter mode: encrypt
Enter shift: 2
ECV
Example 2 (running from main.py)
Enter text: ECV
Enter mode: decrypt
Enter shift: 2
CAT
Example 3 (running from main.py)
Enter text: I LOVE CHOCOLATE!
Enter mode: encrypt
Enter shift: 18
A DGNW UZGUGDSLW!
Example 4 (running from main.py)
Enter text: A DGNW UZGUGDSLW!
Enter mode: decrypt
Enter shift: 18
I LOVE CHOCOLATE!
Hint
In Python you can obtain the decimal number corresponding to a given letter using ord().
print(ord('A'))
You can then find the corresponding english character for a given decimal number using chr().
print(chr(65))
Solution
Solution is locked