3.5. Secure Communication and TLS#
To establish secure communication, we need to address three key concerns:
Privacy (Encryption) – Ensures that only the intended recipient can read the transmitted data.
Authenticity (Signing) – Ensures that the sender of the data is who they claim to be.
Trust (Certificates & Certificate Authorities) – Provides a way for users to verify the identity of the entity they are communicating with.
Together, these techniques enable end-to-end secure communication, forming the foundation of web security.
3.5.1. Transport Layer Security (TLS)#
Transport Layer Security (TLS) is a widely used protocol that implements secure communication by combining the aforementioned techniques into a standardised protocol.
TLS is a general protocol for secure communication and is used in applications such as securing the web, email, instant messaging protocols and voice/video calls.
Note
TLS was formerly known as “Secure Sockets Layer” or SSL.
3.5.2. TLS Handshake#
Before two parties can communicate securely, they must establish a TLS session. Establishing a session is accomplished by a handshake process.
Typically TLS is used for client-server communications, so we will use that terminology for the remainder of this page.
Handshake Steps
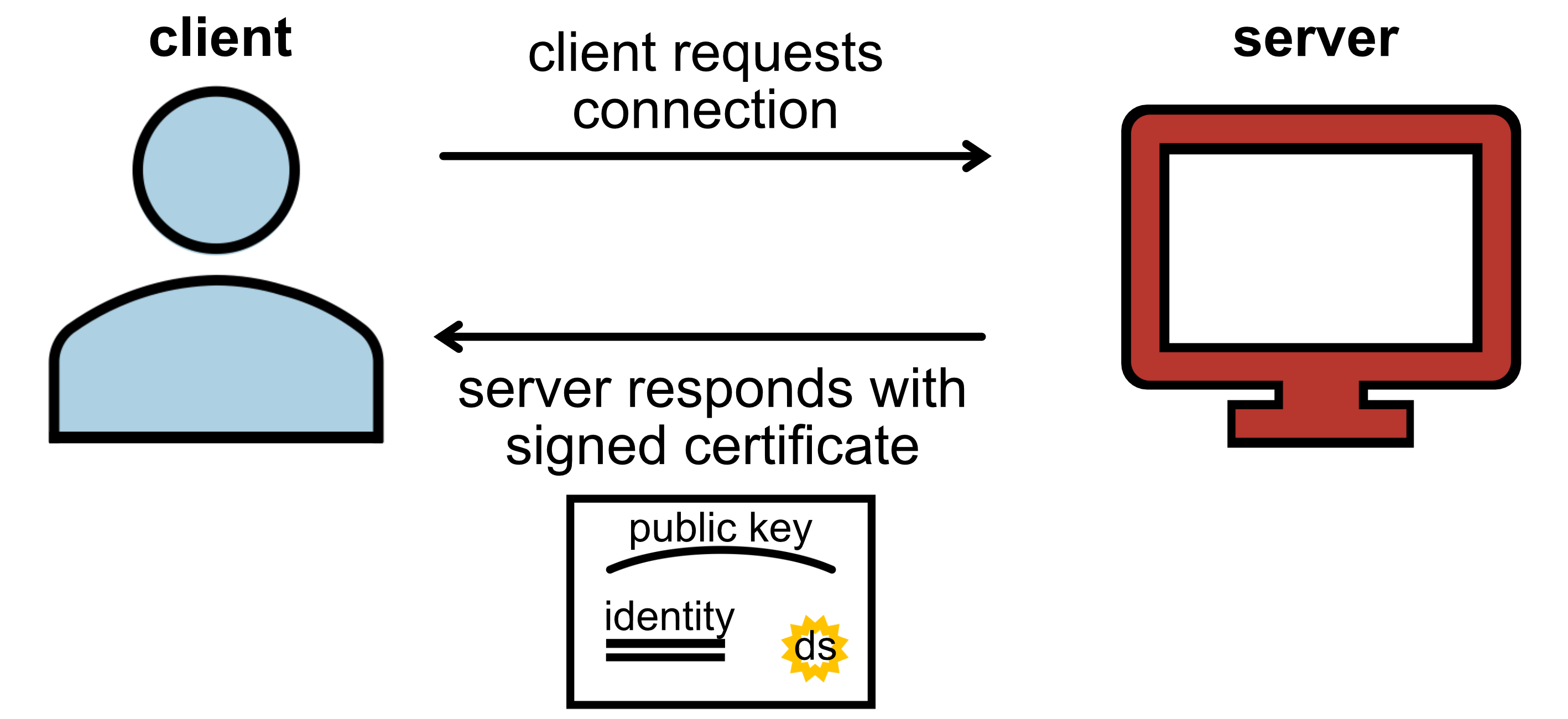
The client sends the server a request for a secure connection
The server responds to the client with its certificate
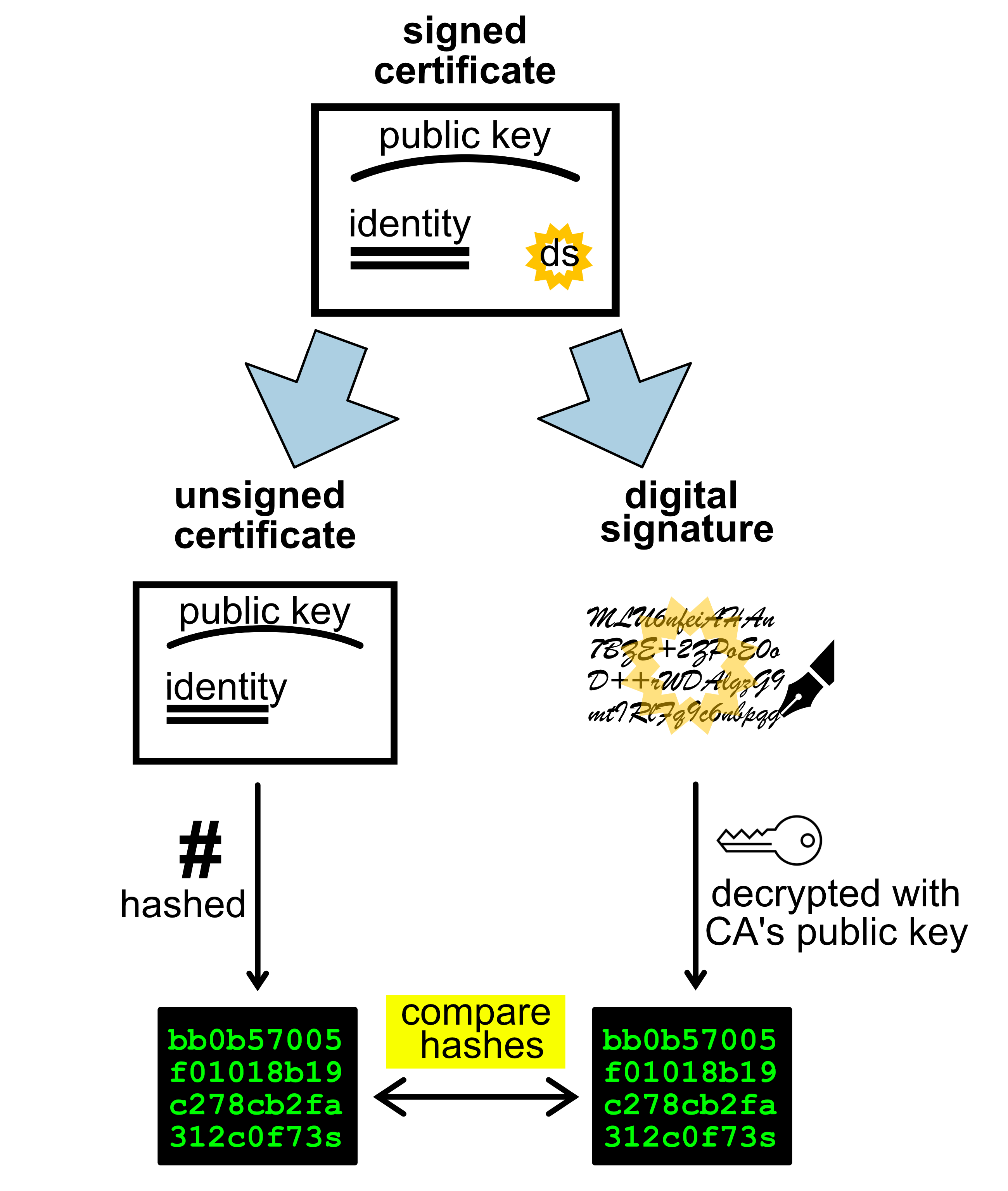
The client checks the validity of the certificate using the CA’s public key, thus confirming the identity of the server
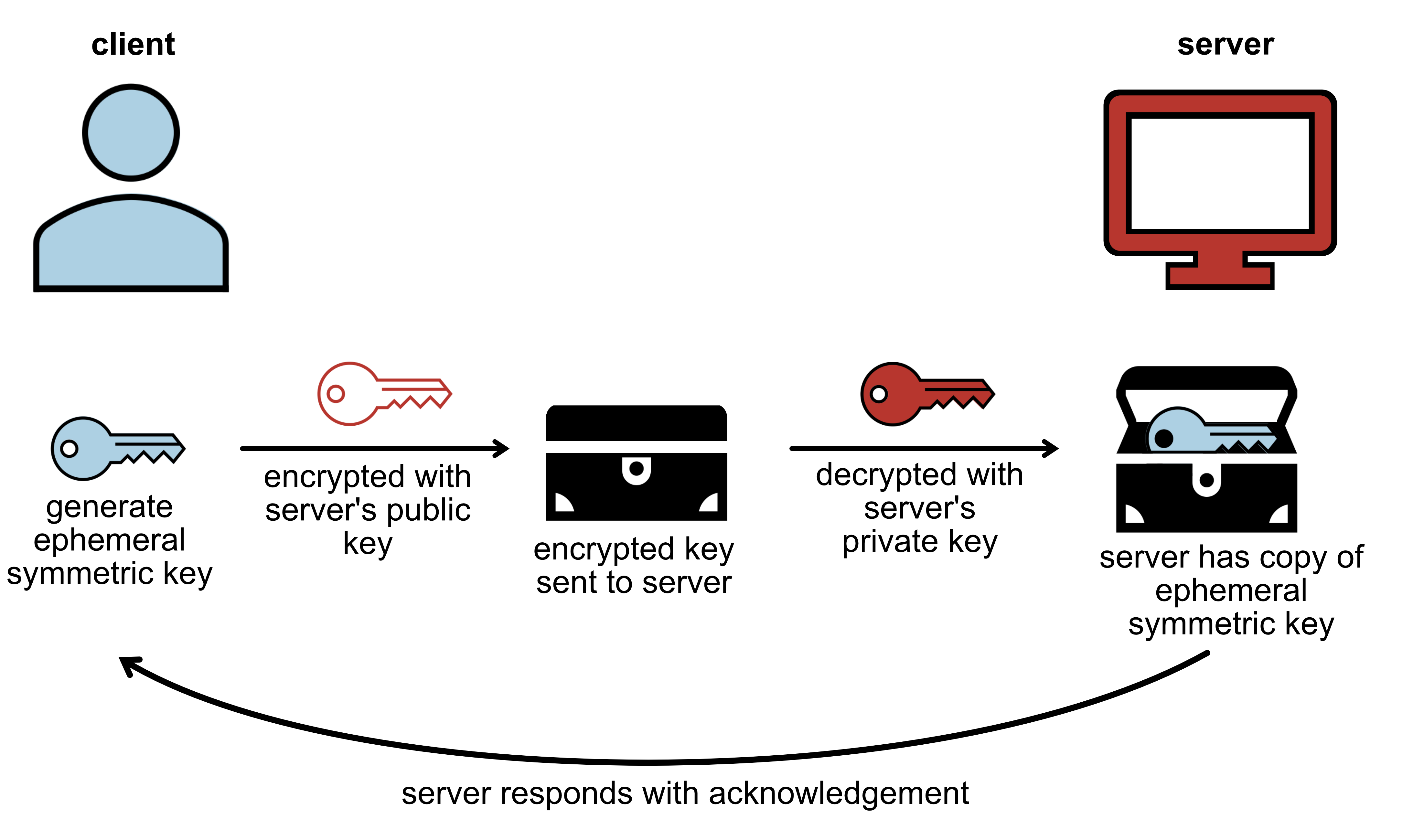
The client generates an ephemeral symmetric key, which will be used for the duration of the session
The client encrypts the symmetric key with the server’s public key
The client sends the encrypted key to the server
The server acknowledges the exchange
Now both the client and the server can communicate securely using the ephemeral symmetric key.
3.5.3. TLS Session#
After a successful handshake, we say that a “session” has been established.
Asymmetric encryption is slow and can only encrypt data up to the length of the key. Therefore for the remainder of the session the symmetric key, that was generated by the client, is used to encrypt the data transferred between client and server.
A session is ended either by:
an explicit termination message sent by either client or server
a time period being reached in which no communication occurs
The timeout period can be mutually agreed during the first two steps of the handshake. Once a session is ended, the client needs to repeat the handshake process to re-establish a session.